PasswordLess authentication is coming and fast. In Microsoft Ignite there were multiple sessions regarding passwordless authentication and announcement of phone sign-in to Azure Active Directory using the Microsoft Authenticator App. This blog post summarizes my own experiences of using this new cool feature.
How to enable passwordless authentication in Azure AD in a nutshell:
- Download and install newest Azure AD Preview PowerShell module
- Connect to Azure AD with Global Admin or Security Admin account
- Run PowerShell command which creates new Azure AD policy for your organization
- Enroll Azure MFA for a user
- Installation of the latest version of Microsoft Authenticator (iOS 8.0 or Android 6.0 minimum) with push notifications added to the application
Download and install the module
Nothing new in here but if you face an error below use -AllowClobber switch to install the module.
Install Azure AD Preview module
Configure Tenant
New Azure AD policy needs to be created to the tenant. As seen below I had a B2B policy in place in my tenant already.
New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault $true -DisplayName AuthenticatorAppSignIn
Register Phone and Enable Phone Sign-in
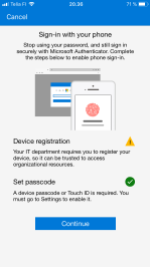
Phone registration is a requirement which needs to be fulfilled. This can be achieved from the Authenticator App.
In the last picture on the right, you can see the icon  which shows that phone sign-in is enabled.
which shows that phone sign-in is enabled.
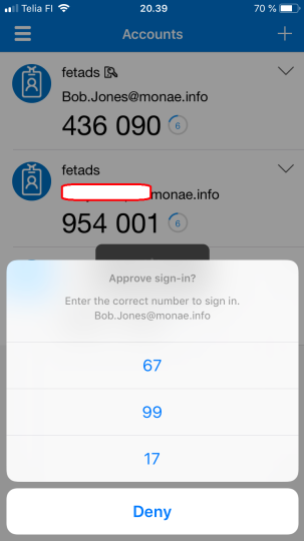
How it looks in action
End-user experience is smooth and fast, and no typing of passwords. The video below shows experience from a cloud-only user sign-in and pictures from the Microsoft Authenticator App during flow
Configuration & Troubleshooting – hybrid identity scenario in a federated environment (AD FS)
When I was configuring phone sign-in to a user who is from a federated environment I was struggling to get it working. First got an error from Microsoft Authentication App (on the left) and then tried to configure the Microsoft Company Portal App to perform device registration to AAD where I got an error on the right. Because of my iPhone troubleshooting skills, I was banging my heads to the wall quite heavily at this point.
After investigation I found this from Microsoft Company Portal (Intune) App:
Error with code: -1202 Domain: NSURLErrorDomain ProtocolCode:(null) Details:The certificate for this server is invalid. You might be connecting to a server that is pretending to be “monaegroup1-adfs1.westeurope.cloudapp.azure.com” which could put your confidential information at risk.. Inner error details: Error domain: NSURLErrorDomain
Code: -1202
Description: The operation couldn’t be completed. (NSURLErrorDomain error -1202.)
User info: {
ADBrokerVersionKey = “6.0.5”;
}
In the past I have been working multiple years with PKI and this error leads me to untrusted certificate problem, iPhone was not able to verify the certification chain and for that reason, authentication is not successful. I exported my root certificate and just in case the adfs certificate public portions and installed those to iPhone, so in summary:
- ADFS public certificate
- Root CA public certificate
- Remember to add Root CA certificate as trusted in iPhone settings (settings-general-about-certificate trust settings-enable full trust for root certificates
How it looks in action – user in hybrid identity scenario (AD FS)
Caveats (docs.microsoft.com)
ADFS – Authentication is always by default sending notification for approval which prevents the user from redirected to ADFS for sign-in verification without user interaction and selecting “use your password instead” in Hybrid tenant scenario. This process will also bypass any on-premises Conditional Access policies, and Pass-through authentication flows. The exception to this process is if a login_hint is specified, a user will be auto-forwarded to AD FS, and bypass the option to use the password-less credential.
MFA Server – End users who are enabled for MFA through an organization’s on-premises Azure MFA server can still create and use a single password-less phone sign-in credential. If the user attempts to upgrade multiple installations (5+) of the Microsoft Authenticator with the credential, this change may result in an error.
Device Registration – When user enabled phone sign-in for the identity phone needs to be registered to the tenant. There is single tenant limitation currently which means that only one work or school account in the Microsoft Authenticator app can be enabled for phone sign-in.
Summary
I have been eagerly waiting for this feature to be published to Azure AD also because have been using it with my LiveID since it was released. The feature is easy to deploy and more easy to use. Hopefully, this post avoids you to face similar problems than I had with phone registration. Naturally, these are not ahead when using real production environment where publicly trusted certificates are in use.