Updated 04/08/2018
Update ADFS SSL Certificate Through AADC
————————————————————————————————————————————
Windows Server 2012 R2 running ADFS
“Replacing the SSL and Service Communications certificates go hand-in-hand. Any time you are replacing one of these certificates, you must also replace the other. SSL certificates exist on all Federation Servers and Federation Server Proxy servers. Service Communications certificates only exist on Federation Servers”.
As you already know AD FS in W2012 R2 is not dependent from IIS anymore. IIS is running at top of HTTP.sys so configuration is a little different than with earlier operating systems.
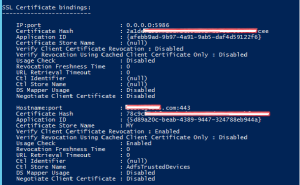
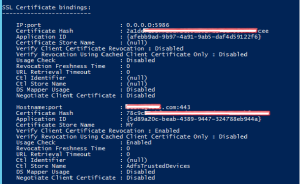
netsh http show sslcert – show current ssl binding of machine. As you can see there is certificate with name and port xxx.com:443 with thumbprint starting 78c9…..
If SSL certificate needs to be changed following tasks needs to be done:
- Import the new certificate to the Machine’s Personal Store
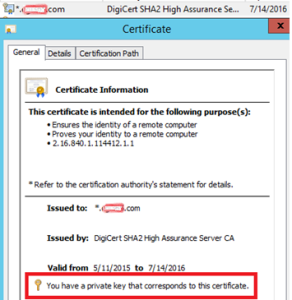
- Make sure you have a private key that corresponds to this certificate. If not, go to the PC you requested the certificate on, export it from there and make sure to include the private key.
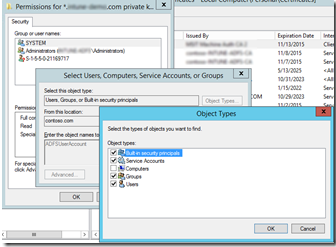
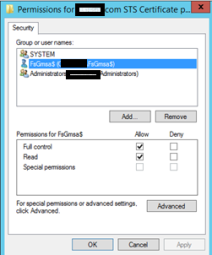
- Assign the proper permissions to the Private Key for the ADFS Managed Service Account:
- Make sure to select “Service Accounts” in when searching for the account if using gMSA account as service account
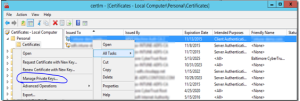
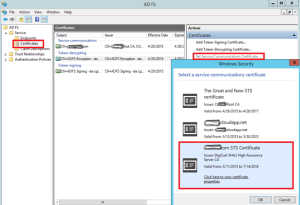
- Open AD FS management and go to Certificates and select “Set Service Communication Certificate”
Prompt will open and you can select certificate. If you don’t see the new certificate in the list of available certificates
- you either don’t have the private key that corresponds to this certificate
- you didn’t import the cert correctly
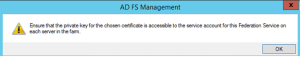
When certificate is changed warning about private key access will show up.
After changing the certificate from ADFS service you need to configure certificate bindings via PowerShell and Netsh
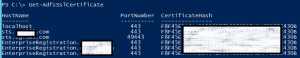
- Run Get-AdfsSslCertificate. Note the thumbprint of the new certificate.
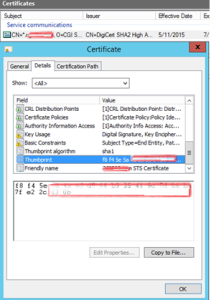
If it’s unclear which certificate is new, you can confirm certificate thumbpring from certificates mmc console.
- Run Set-AdfsSslCertificate -Thumbprint <your certificate thumbprint> (thumbprint of the new certificate without spaces). Note hidden mark as first letter at thumbprint!!
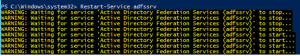
Restart the ADFS service
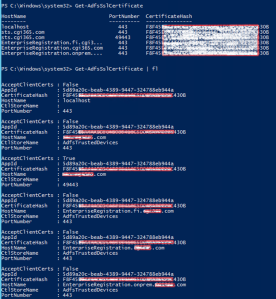
- Confirm change Get-AdfsSslCertificate command. All endpoints should have new certificate (thumbprint)
- NOTE! Set-ADFSSslCertificate command needs to be run on the primary ADFS server
Web Application Proxy (WAP)
- Copy and import the new certificate to the Web Application Proxy/Proxies to Machine personal store
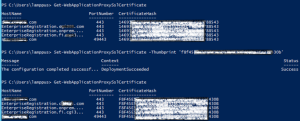
- Switch the certificate on the Web Application Proxy, and place certificate with “Install-WebapplicationProxy or “Set-WebApplicationProxySslCertificate” cmdlets
- $FScred = Get-Credential
- Install-WebApplicationProxy -FederationServiceName “xxx.com” -FederationServiceTrustCredential $FScred -CertificateThumbprint “your ssl certicate thumbprint“
“Set-WebApplicationProxySslCertificate” cmdlet.
Set-WebApplicationProxySslCertificate -Thumbprint “your ssl certicate thumbprint”
NOTE! Do this on all of yout WAP servers!!
Windows Server 2008 R2 running ADFS
Windows Server 2008 R2 is using IIS so changing Service Communications certificate process is slighty different. Process from ADFS console are identical.
- Import the new certificate to the Machine’s Personal Store
- Make sure you have a private key that corresponds to this certificate.
- Assign the proper permissions to the Private Key for the ADFS Managed Service Account
- Make sure to select “Service Accounts” in when searching for the account if using gMSA account as service account
- Switch to AD FS management, drill down to Certificates and select “Set Service Communication Certificate”
You will be prompted for the required certificate. If you don’t see the new certificate in the list of available certificates – it means you either don’t have the private key that corresponds to this certificate OR you didn’t import the cert correctly.
When certificate is changed warning about private key access will show up.
When certificate has been changed IIS bindings need to be changed with following steps (guidance from MS site)
- Open Internet Information Services (IIS) Manager
- In the Connections pane on the left, expand your server name, expand Sites and select the site used by ADFS (Default: Default Web Site)
- Right-click on the site name and select Edit Bindings
- Highlight the SSL port (Default: https/443), click Edit and select the new SSL certificate from the drop-down list.
- NOTE: Your old and new SSL certificates will likely have the same subject name and will look the same in the list. Select either and click View to make sure you are setting the correct one.
- Click OK, click Close and close the IIS Manager console
- Under elevated command prompt, run iisreset.exe so that the new certificate is taken into use.
NOTE! Set-ADFSSslCertificate command needs to be run on ALL ADFS servers
False, only primary member can change the settings.
Thanks for the heads up! At the time of writing it was so. I need to update the doc to the current state.
thanks a lot! you saved my day
Great to hear😊