Staying ahead of potential threats is a top priority for organizations worldwide in the ever-evolving cybersecurity landscape. Modern and effective cybersecurity defenses are built on several essential pillars, where security posture management plays an important role.
Microsoft’s Security Exposure Management (XSPM) solution is a new innovation in the posture management domain. It can be imagined as a combination of the next-generation vulnerability management & posture management solution that modernizes posture management in the same way XDR modernizes threat management. Where XDR (detect, investigate, and respond) provides unified threat management for workloads, the XSPM (identify and protect) provides unified exposure management for the same workloads (see figure below – initial version from Microsoft Secure presentation).

XSPM is taking its early steps and is in the public preview phase while writing this blog. There is definitely more to come, and I am eagerly waiting to see how the solution will improve in the future.
Because of XSPM’s complexity behind the scenes, I decided to create a blog series about it. In the first part of the series, I will cover the overall benefits of leveraging the solution and how to address initiatives, underlying metrics, recommendations, and events.
The second part will focus on the ‘Exposure Graph’ and attack surface, how to leverage the exposure graph map and attack path features, how the latter differs from Defender for Cloud’s attack path analyses, and the Secure Score role in the future without forgetting the raw data that can be used through Defender XDR advanced hunting.
Exposure Management Framework
What is Microsoft Security Exposure Management? According to Microsoft: ‘Microsoft Security Exposure Management is a security solution that provides a unified view of security posture across company assets and workloads. Security Exposure Management enriches asset information with a security context that helps you to manage attack surfaces, protect critical assets, and explore and mitigate exposure risk‘.
The key components of Microsoft’s Security Exposure Management framework are designed to provide a comprehensive approach to environment security posture, addressing a holistic view of potential vulnerabilities and threats. Here are available integrations for Security Exposure Management (at the time of writing, list from MS blog):
- Vulnerability Management (VRM)
- Microsoft Defender Vulnerability Management (MDVM)
- Qualys Vulnerability Management (Preview)
- Rapid7 Vulnerability Management (Preview)
- External Attack Surface Management (EASM)
- Microsoft Defender External Attack Surface Management
- Cloud Security (CSPM)
- Microsoft Defender Cloud Security Posture Management (CSPM)
- Endpoint Security (Device Security Posture)
- Microsoft Defender for Endpoint (MDE)
- Identity Security (ISPM)
- Microsoft Defender for Identity (MDI)
- Microsoft Entra ID (Free, P1, P2)
- SaaS Security Posture (SSPM)
- Microsoft Defender for Cloud Apps (MDA), including connectors to SaaS applications
- Email Security
- Microsoft Defender for Office (MDO)
- OT/IOT Security
- Microsoft Defender for IoT
- Asset & Configuration Management
- ServiceNow CMDB (Preview)
- Secure Score
XSPM unifies data across the entire security stack. It already has native integrations with other Microsoft security solutions, and there are more to come, as seen below (figure from Microsoft—https://bit.ly/3xKHQM7). With XSPM, you can connect your security solutions, infrastructure tools, and third-party solutions to bring visibility into cloud and on-premises assets.

At the time of writing, if you want to integrate non-MS solutions to XSPM, you can express interest in joining early pioneers in the Defender XDR portal to get data from third-party solutions through a connector (ServiceNow CMDB, Qualys, and Rapid7 are available on the XDR portal).

Pre-Requisites
Microsoft Security Exposure Management workspace is provisioned out of the box to the Defender XDR portal but needs data from deployed solutions. In a nutshell, the more comprehensive the deployment, the wider the coverage. For example, to get complete data from Defender for Cloud, you must enable DCSPM for your subscriptions.
Also, you need permission to access the data (such as MDE device groups, identities, etc.) to see all the content and relations between the data. To summarize, you need one of the following permissions:
- Global Admin (read and write permissions)
- Global Reader (read permissions)
- Security Admin (read and write permissions)
- Security Operator (read and limited write permissions)
- Security Reader (read permissions)
Detailed information about prerequisites is found here.
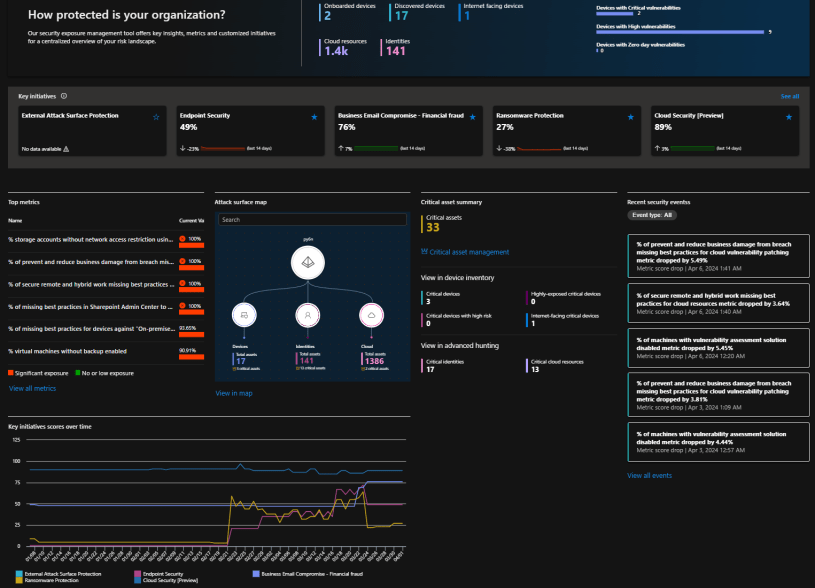
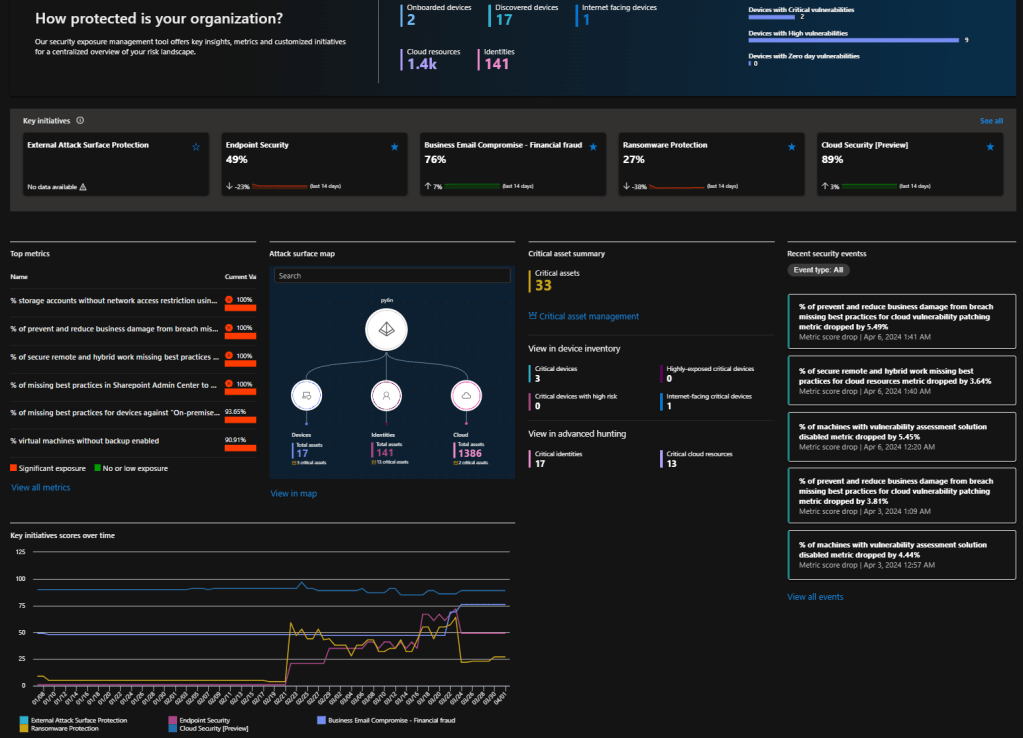
Overview Dashboard
The Microsoft Security Posture Management (XSPM) dashboard provides a centralized view of the organization’s security posture status, understanding the most critical risks in a single view. It integrates various components (listed above) of security data, allowing for efficient management and effective prioritization of security risks.
The dashboard shows the number of assets, key initiatives, top metrics, attack surface map, recent security events, critical assets summary, and key initiatives scores over time.
Exposure Insights
Understanding and having visibility into your organization’s assets is an important part of modern security defenses. By utilizing exposure insights, decision-makers, risk owners, and security teams can gain valuable context around their asset inventory’s security state. For example, I’ve seen too many environments where the organization has deployed the Defender XDR solution. Still, the configuration hasn’t been finalized and is not up-to-date, and XSPM can help in this area.
Exposure insights include security events, recommendations, metrics, and initiatives. These components provide a detailed and granular view of the security posture state, enabling organizations to proactively mitigate potential risks. Exposure insights enable:
- Break down organizational security posture into prioritized initiatives
- Measure and track exposure of key security elements within initiatives
- Prioritize areas of security focus based on initiatives and metrics
- Follow actionable remediation steps to improve security posture and reduce risk
- Track improvements in security initiatives to track security risk reduction
Initiatives
During the past years, I have been lucky to be involved in several cloud security posture management cases in multi-cloud environments. One could say that managing security posture can be complicated, but implementing XSPM and security initiatives can simplify the process. XSPM initiatives can help organizations assess their readiness and maturity in specific security risk areas. The idea behind the initiatives is to simplify posture management and help organizations assess readiness and maturity.
XSMP provides predefined initiatives, each containing one or more security metrics relevant to that initiative. These initiatives can focus on specific workload domains, such as endpoint, identity, and cloud security, or they can relate to specific threats across multiple categories, such as ransomware protection or critical asset protection. Additionally, initiatives can also help you meet specific compliance standards.

When you drill down to individual initiatives, you can evaluate all security metrics, recommendations, and history from the initiative page. It’s a great way to start improving an organization’s security posture, and by using initiatives, you can more easily track bigger entities than through Microsoft Secure Score.
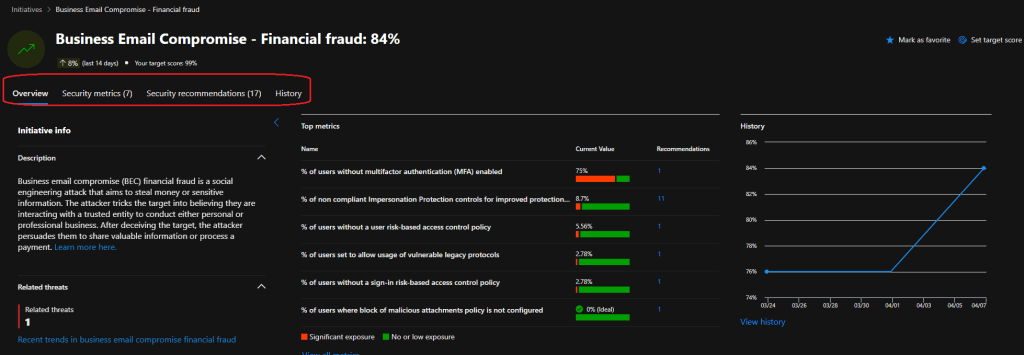
Initiative score
The initiative score is calculated based on the value and weight of the associated metrics. It rises as metrics improve, reflecting a better posture in the initiative domain.
- Metrics largely improve by applying the recommendations associated with the initiative.
- Recommendations are fixed, metrics rise, and initiative scores rise to reflect improved security posture.
- Changes in metrics, including deprecation/removal, value, and metric properties, can affect the initiative score.
Security teams can also set target score per initiative as can be seen from below BEC initiative.




Metrics
Metrics group recommendations for similar assets and measure security exposure around those assets, from very high exposure to no exposure identified.
For example:
- % of users without multifactor authentication (MFA) enabled
- % of users without a user risk-based access control policy
Each metric shows:
- The percentage of assets affected, the metric’s relative importance, and the metric affects an initiative.
- It also shows the metric’s weight or importance and its effect on the initiative score as a number. One is the lowest, and 10 is the highest.
- Metric weight can be customized to have greater or lesser effect based on organizational business priorities.
- Editing metric weight value affects the metric and all related initiatives.
Most metrics have at least one associated recommendation but can have more, as in the example below, which has 11 different recommendations.

Recommendations
Other Microsoft solutions, such as Defender for Cloud with DCSPM-enabled, Defender XDR Secure Score, and other MS and non-MS solutions where XSPM can ingest data, are sources for the recommendations. Microsoft’s Secure Score documentation states that assets and workloads are assessed against security measurements and standards, and security recommendations are issued based on those assessments.
It’s important to highlight that the XDR portal’s recommendations include the following statement: ‘These recommendations are based on global compliance considerations and may not necessarily relate to specific aspects of this initiative.’

As you can see, the recommendations look very familiar if you have been using the Secure Score (including recommendations for supported SaaS applications).

Security events
Security events in Microsoft Security Exposure Management track initiative and metric score drop incidents to determine how they affect organizational security posture. With events and history blades, whoever uses XSPM can effectively track how posture score has been living in its own environment.


API Support
To the best of my knowledge, API support is not currently available. If you have more information, please let me know. On the other hand, you have raw data in Defender XDR advanced hunting and access to the exposure graph through the attack map.
Summary
This blog provided an overview of Microsoft’s Security Exposure Management solution. As wrote earlier, XSPM is taking its early steps and is in the public preview phase while writing this blog. There is definitely more to come, and I am eagerly waiting to see how the solution will improve. For example, you cannot do any exclusion for now like you can in Secure Score in MDC or Defender XDR. This would be a handy feature because the current way of adding all the entities might give a wrong impression of your overall posture state.
One important point I need to highlight here is licensing. For now, XSPM is available to customers on the Defender XDR portal. However, the product site FAQ section states, ‘Pricing and licensing are still under evaluation. We’ll have more to share in the coming months’.
The next part will explore the raw data, exposure graph, and workload relations from a threat perspective. Stay tuned!
References
Introducing Microsoft Exposure Management
What is Microsoft Security Exposure Management?
Compare Microsoft Security Exposure Management with Secure Score