Last spring, I teamed up with the amazing Raghavendra Boddu on a book project that consumed our days and nights for nine months, starting in July 2023 and ending in March 2024. During that time we cooked up something in cybersecurity that we believe will bring value to our community. Our book Microsoft Unified XDR and SIEM Solution Handbook was initially announced at the end of February, but I also wanted to share some insights in my blog.
Background
This project has been a great effort, and we’re looking forward to sharing insights, stories, and practical tips in the upcoming book. This book delves deep into the powerful Microsoft Unified XDR and SIEM Solution, breaking down its capabilities and advantages and demonstrating its effectiveness against real-world attack scenarios. Think of it as your one-stop shop for mastering Microsoft’s Unified Solution.
We’ve included a case study featuring a fictional company to bring the theory to life. This scenario showcases the security solutions in action, illustrating their real-world effectiveness and potential impact on organizations. We did our best to get the most important stuff right, even though we know some things are bound to change and there will always be limits. But the main ideas and groundwork stay the same, no matter what updates come along.
What this book covers?
Here are chapter introductions, starting from Chapter 0 – case study and ending up to Chapter 10 – use full resources.
Chapter 0, Case Study, considers a scenario of driving digital transformation and security enhancement at High Tech Rapid Solutions Corp (a fictional company name we will use throughout this book).
Chapter 1, Introduction to Zero Trust, lays the groundwork for understanding why XDR and SIEM solutions are crucial by delving into the concept of Zero Trust: its importance, principles, architecture, implementation considerations, and significance for security operations. We’ll explore these topics in detail with practical recommendations, building a solid foundation for your decision-making.
Chapter 2, Introduction to XDR and SIEM, dives deep into the world of XDR and SIEM, explaining their core functions and why they’re essential for modern cybersecurity. It explores their true capabilities, practical use cases, implementation strategies, and untangling buzzwords such as EDR, MDR, NDR, and SIEM along the way. Ultimately, it proposes a solution to break down siloed security architectures and streamline SOC operations, empowering analysts with improved triaging, investigation, and threat-hunting tools.
Chapter 3, Microsoft’s Unified XDR and SIEM Solution, dive deep into Microsoft’s unified XDR and SIEM solution, showcasing its seamless integration and benefits. It then explores each defender within Microsoft Defender XDR (MDE, MDI, MDO, MDA, and MDC) and Microsoft Sentinel, the SIEM and SOAR solution. Finally, it makes a compelling case for why adopting this unified approach can break down siloed security tools and propel your enterprise to a new level of protection.
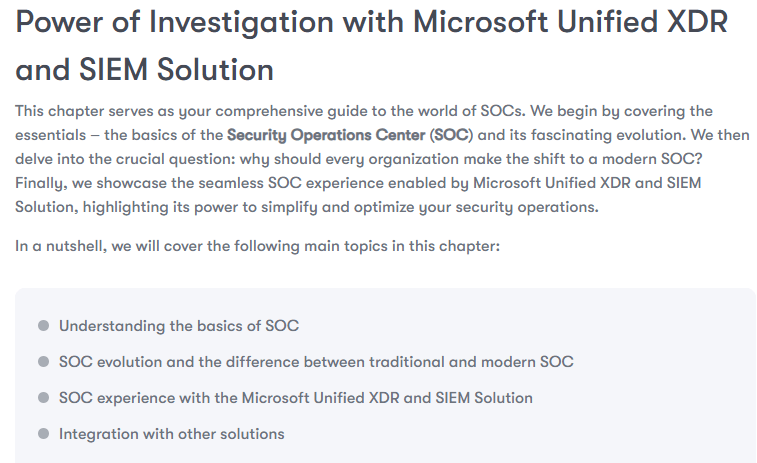
Chapter 4, Power of Investigation with Microsoft’s Unified XDR and SIEM Solution, delves into how Microsoft’s unified XDR and SIEM solution empowers enterprises to revamp their SOC, streamlining daily operations and life cycle management. It explores this integration’s critical benefits over traditional siloed technologies, enabling faster threat response and enhanced triaging, investigation, and remediation workflows.
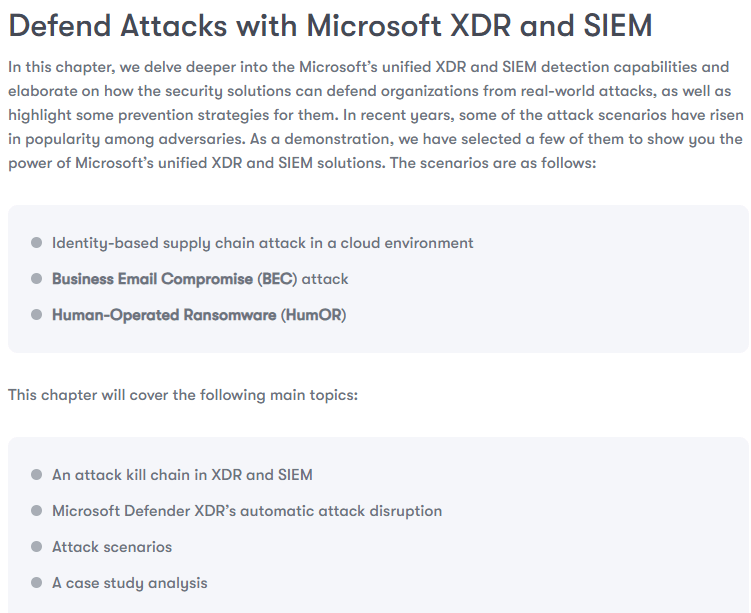
Chapter 5, Defend Attacks with Microsoft’s Unified XDR and SIEM, examines the application of Microsoft’s unified XDR and SIEM solution in safeguarding organizations against cyber threats such as identity-based supply chain attacks in cloud, human-operated ransomware (HumOR), and business email compromise (BEC) attacks. Beyond a thorough analysis of the threat landscape, practical demonstrations of these tools’ effectiveness will be covered.
Chapter 6, Security Misconfigurations and Vulnerability Management, delves into the critical nature of security misconfigurations and vulnerabilities, outlining a high-level vulnerability management process and showcasing how Microsoft’s unified XDR and SIEM solution tackles these challenges head-on.
Chapter 7, Understanding Microsoft Secure Score, empowers you to strengthen your organization’s security posture by navigating effective strategies to boost your Secure Score and understanding the reasoning behind each recommendation.
Chapter 8, Microsoft XDR and SIEM Implementation Strategy, Approach, and Roadmap, guides you through successfully implementing Microsoft’s unified XDR and SIEM solution, highlighting crucial topics such as assessments, strategic considerations, and best practices for effective adoption and deployment.
Chapter 9, Managed XDR and SIEM Services, examines the fundamentals and advantages of these services and reveals how their effective management can shield you against a wide spectrum of cyber threats.
Chapter 10, Useful Resources, offers valuable resources to sharpen your skills in Microsoft’s unified XDR and SIEM solution, empowering you to confidently defend your organization against evolving threats.
Book Structure – Parts 1, 2 and 3
The book contains three parts which are:
- Part 1 – Zero Trust, XDR, and SIEM Basics and Unlocking Microsoft’s XDR and SIEM Solution
- Part 2 – Microsoft’s Unified Approach to Threat Detection and Response
- Part 3 – Mastering Microsoft’s Unified XDR and SIEM Solution – Strategies, Roadmap, and the Basics of Managed Solutions
The next section contains descriptions from the each part and some insights from each chapter when you take a look on the figures below.
Part 1 – Zero Trust, XDR, and SIEM Basics and Unlocking Microsoft’s XDR and SIEM Solution
This part breaks down the basics of Zero Trust, XDR, and SIEM and explains why you should consider using XDR and SIEM together, especially Microsoft’s unified XDR and SIEM solution. It’s like having a security toolbox with all the right tools for the job, making it easier to protect yourself from cyber threats.
- Chapter 1, Introduction to Zero Trust
- Chapter 2, Introduction to XDR and SIEM
- Chapter 3, Microsoft’s Unified XDR and SIEM Solution




Part 2 – Microsoft’s Unified Approach to Threat Detection and Response
This part dives deep into the game-changing power of Microsoft’s unified XDR and SIEM solution. We’ll explore how it transforms the SOC’s journey, streamlines its work, and shields organizations against real-world threats. We’ll dissect prevention strategies, tackle misconfigurations and vulnerabilities, and unveil the vital role of Secure Score and monitoring in this unified security shield. Brace yourself for a comprehensive exploration of how this solution simplifies and strengthens your cyber defenses.
This part has the following chapters:
- Chapter 4, Power of Investigation with Microsoft’s Unified XDR and SIEM Solution
- Chapter 5, Defend Attacks with Microsoft XDR and SIEM
- Chapter 6, Security Misconfigurations and Vulnerability Management
- Chapter 7, Understanding Microsoft Secure Score



Part 3 – Mastering Microsoft’s Unified XDR and SIEM Solution – Strategies, Roadmap, and the Basics of Managed Solutions
This part guides you through key assessments, strategies, and managed service options to smoothly adopt and implement this unified security solution. We emphasize the importance of starting with a thorough assessment and a clear strategy to maximize the benefits of XDR and SIEM. Additionally, we explore the basics of managed security services in the Microsoft ecosystem, focusing on the generic Managed Security Services Provider (MSSP) framework and some useful resources.
This part has the following chapters:
- Chapter 8, Microsoft XDR and SIEM Implementation Strategy, Approach, and Roadmap
- Chapter 9, Managed XDR and SIEM Services
- Chapter 10, Useful Resources




Greetings
I want to express my heartfelt gratitude to Rod Trent for writing the insightful ‘Foreword’; it means a lot to us! Special thanks to our dedicated Technical Reviewers, Thomas Naunheim & Harri Jaakkonen, for their efforts and engaging sparring sessions throughout the project. A special shout-out to my amazing co-author, Raghavendra Boddu [Raghu], for trusting me, having a seamless partnership, and making our project a reality. It has been a privilege to work with you during the past months!
Kudos to my community friends Joosua Santasalo & Sakari Pajulampi for their deep dive sparring sessions related to complex attack scenarios, how to defend the attacks, and Armando Penunuri’s contributions.
You can get your copy here:
- Amazon – https://lnkd.in/dWR7rtFi
- Pack – https://bit.ly/3y9Dajq
- OReilly – https://bit.ly/4bfjuJ4
- Apple Books – https://bit.ly/3UKyvNx
- Barnes & Noble – https://bit.ly/3Qxfqf4
Amazon QR code

We hope this works for you and are always open to hearing your thoughts. We’re here to learn and grow!
Excellent consolidation! Very agnostic and holistic point of view.