In recent months there have been several reports indicating O365 users as the target in a phishing campaign and It’s quite obvious that one of the main targets are high privileged accounts. In Microsoft ecosystem Azure AD provides many features to protect high privileged accounts in the cloud (MFA, PIM, Identity Protection, attack detection and conditional access). Privileged Identity Management (PIM) provides now support for AAD roles and Azure RBAC, launched while ago (in preview mode in time of writing).
PIM Licensing (docs.microsoft.com)
Azure AD Privileged Identity Management is available as part of the Premium P2 edition of Azure AD. In general Azure AD P2 or EMS E5 is needed to activate PIM in tenant.
Enable PIM to tenant
- Sign in to the Azure AD portal (portal.azure.com or aad.portal.azure.com) as a global administrator and select the tenant where you want to activate PIM. If you have more than one tenant, navigate to right corner in Azure portal and choose the correct one
- Select More services and search for Azure AD Privileged Identity Management and click Create (after created PIM management console should open).
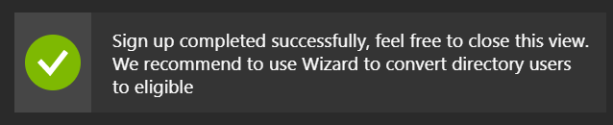
- If you navigated straight to aad.portal.azure.com as I did (pictures below) PIM management console is already visible but you need to signup for PIM and verify identity before it can be used



Overview of PIM Management
Managing PIM is separated to different sections. From main page (Navigation Panel) you can manage all PIM related tasks.

Roles description (from docs.Microsoft.com)
My Roles – displays a list of eligible and active roles assigned to you. This is where you can activate any assigned eligible roles.
Approve Requests – displays a list of requests to activate eligible Azure AD directory roles by users in your directory, which you are designated to approve
Pending Requests – displays any of your pending requests to activate eligible role assignments.
Review Access lists – active access reviews you are assigned to complete, whether you’re reviewing access for yourself or someone else
Azure AD directory roles – located under the manage section of the left navigation menu displays the dashboard for privileged role administrators to manage role assignments, change role activation settings, start access reviews, and more (dashboard is disabled for anyone who isn’t a privileged role administrator)
Azure Resource roles – located under the manage section of the left navigation menu displays a list of subscription resources you have role assignments choose
Privileged Role Management
Roles which are managed with PIM:
- Global administrator
- Privileged role administrator
- Billing administrator
- Password administrator
User management administrator - Exchange administrator
- SharePoint administrator
- Skype for Business administrator
Roles not managed with PIM:
- Both Exchange Online and Sharepoint Online contains other administrative roles which are not managed through PIM. Only roles mentioned above are included in PIM. Same goes with Intune, at least at time of writing you cannot manage Intune roles through PIM.
Eligible vs Permanent Roles
By default all roles are set as permanent when user is added member of administrative group. PIM introduces new mode, eligible permission. This means that when you have for example eligible Global Admin permission you need to activate role when you are performing tasks which needs GA permission (just-in-time admins). If you are using eligible roles (which is recommendation when permissions are not needed in daily basis) following tasks are needed to activate role:
- Logon to tenant and navigate to PIM
- Open Azure AD Directory Roles

- Azure AD Directory roles blade opens, from there you can see overall situation of your own roles and other administrators roles from the tenant
- As you can see all the selections are grey which means that I don’t have activated my eligible GA role
- Underneath “Eligible role assignments” – Select Global Admin – Request Activation

- Click Activate and justify reason for permissions

- By default permissions are valid for one (1) hour but this can be changed from settings blade depending on organization needs

- Best practice is that you deactivate your role after task is ready
- Click “Active Role Assignments” from AD Directory Roles dashboard

- Click deactivate

Settings
Settings regarding Roles, Alerts and Access Reviews can be configured from settings tab depending on organization security policies.



Wizard
From wizard blade you can discover all PIM manageable roles and convert user permissions from permanent to eligible.
Access Review
Microsoft recommends that privileged role administrators should regularly review the roles that user have been given to reduce the risk associated with stale role assignments.
Review can be started from three (3) locations from the PIM:
- Access reviews > Add
- Roles > Review button
- Select the specific role to be reviewed from the roles list > Review button
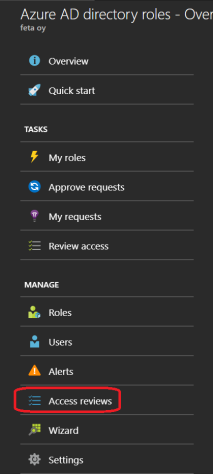
- When you click “Access review” new blade opens where you can configure the review with a name and time limit, choose a role to review, and decide who will perform the review.

Summary
Microsoft has done extremely good work with PIM and implementation is very easy. With PIM you can easily manage, control and monitor access in your organization. It adds more safety to your admin accounts and you can leverage just-in-time admin permissions for admins who doesn’t need permissions in daily basis. With PIM you can manage Azure RBAC roles (preview in time of writing) which brings all PIM capabilities to subscription and resource management.
Worth to mention (from docs.microsoft.com)
- If you’re the first person to run Azure Privileged Identity Management (PIM) for your organization, you will be presented with a security wizard
- After you have made changes, the wizard will no longer show up. The next time you or another privileged role administrator use PIM, you will see the PIM dashboard.
- Before organization starts using PIM, all role assignments are permanent
- It is important that you have at least one global administrator, and more than one privileged role administrator with an organizational account (not a Microsoft account). If there is only one privileged role administrator, the organization will not be able to manage PIM if that account is deleted
- Keep role assignments permanent if a user has a Microsoft account (An account they use to sign in to Microsoft services like Skype and Outlook.com). If you plan to require MFA for activation for that role, that user will be locked out
- Even PIM is enabled I can add members to Global Admin group from O365 management portal. User membership are set as permanent
- If user is membership is eligible she/he is not shown at O365 portal as member of Global Admin group but is shown in PIM management console



Links



