This blog post is all about alert management in M365 security solutions. Even though there are new capabilities launched to the security solutions that make security analysts’ life easier such as Microsoft Defender ATP automatic investigation and remediation you still need to manage incidents and alerts in the Microsoft 365 security solutions. This is the third blog post of the series and earlier ones can be found from securecloud.blog site:
Setting Up The Scene – The Security Providers
What are the security providers? Security providers in Microsoft cloud are the solutions that detect threats & anomalies and create alerts (+ incidents) based on the policies and collected data. These providers send processed alerts also to the Intelligent Security Graph (ISG). At the time of writing, supported security providers in ISG are:
- Azure Security Center (ASC)
- Azure AD Identity Protection (IPC)
- Microsoft Cloud App Security
- Microsoft Defender ATP (MDATP)
- Azure ATP (AATP)
- Office 365
- Azure Information Protection
- Azure Sentinel
Internal Integrations
The picture below doesn’t cover all possible security solutions and integration scenarios, it rather gives overall understanding which solutions can be used to investigate alerts and suspicious activity in the cloud or on-premises.
The best synergy advantages come with the integrations between security solutions. In the top category are the solutions which, in my opinion, are the best ones to start the investigation.
Naturally, if Sentinel is in use it triggers the alert, and the investigation starts from there. It could also be replaced by 3rd party SIEM (Splunk, QRadar, etc). Both Sentinel and Microsoft 365 Threat Protection suite have a rich set of capabilities for investigation and contain a number of data from the user identity, device identity, and network traffic.
Microsoft 365 Security Center which contains Microsoft Threat Protection aka MTP features (launched in early 2020) is the newest addition to the toolbox. Let’s take a closer look at what it brings to the table in terms of alert management in the next chapter.

Options For Alert Management
One of the main challenges with Microsoft security solutions is that alert status is not synced across solutions. Case example could be the following:
- You found alert in MCAS
- Its resource provider is Azure ATP
- You do the necessary investigation and resolve the alert in MCAS
- The alert status still remains as “NewAlert” in Azure ATP, ISG, and new status update is not synced across the solutions
How you can address the problem? Here are a couple of options I tested (not a comprehensive list), take into account that I only tested the solutions that should be capable to handle alerts from other sources than itself only based on documentation:
- Microsoft 365 Security Center with Microsoft Threat Protection (MTP) suite
- Intelligent Security Graph
- Azure Sentinel Playbooks
Microsoft Threat Protection (MTP) Suite
According to Microsoft, M365 Security Center is a new home for monitoring and managing security across your Microsoft identities, data, devices, apps, and infrastructure.
“Microsoft Threat Protection is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks”.
If your environment has proper licenses, the Microsoft Threat Protection suite can be enabled to M365 Security Center. Worth to mention is, it will be enabled automatically to all eligible tenants quite soon, read more from this here.
If you want to read more about the MTP I recommend starting from here. I do not cover MTP in general here, rather focusing on managing incidents & alerts.
Microsoft Threat Protection Suite (MTP) – Game Changer?
I have been struggling with alert management in recent months in multiple environments and it was mind-blowing to see new MTP suite capabilities in M365 Security Center which really helps for managing alerts and incidents.
In M365 Security Center there are incidents & alerts (description from docs.microsoft.com).
- Incidents
- Microsoft Threat Protection connects the dots on individual alerts. Suspicious events that show characteristics of being part of a larger attack are aggregated into an incident.
- Alerts
- The basis of all incidents is alert. Alerts are created when a malicious event or activity is seen on your network. Individual alerts provide valuable clues in what’s happening on individual events or entities.
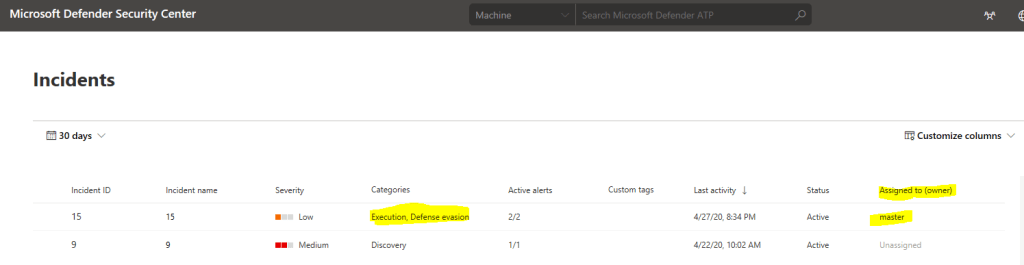
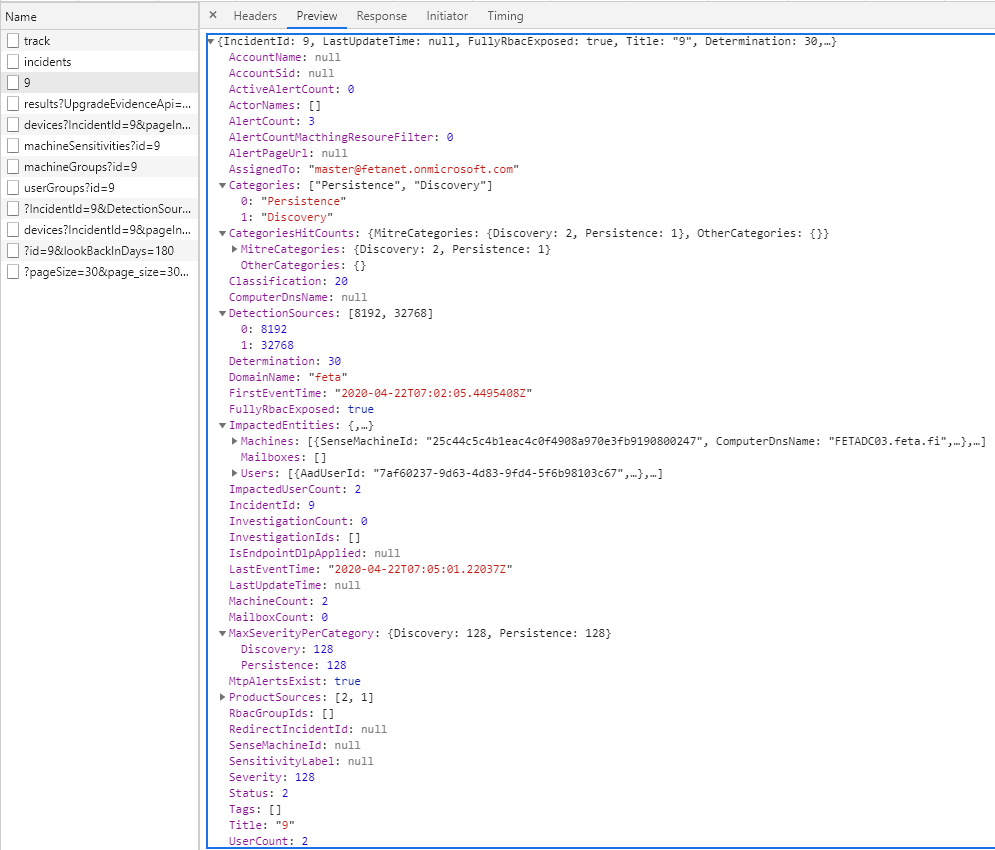
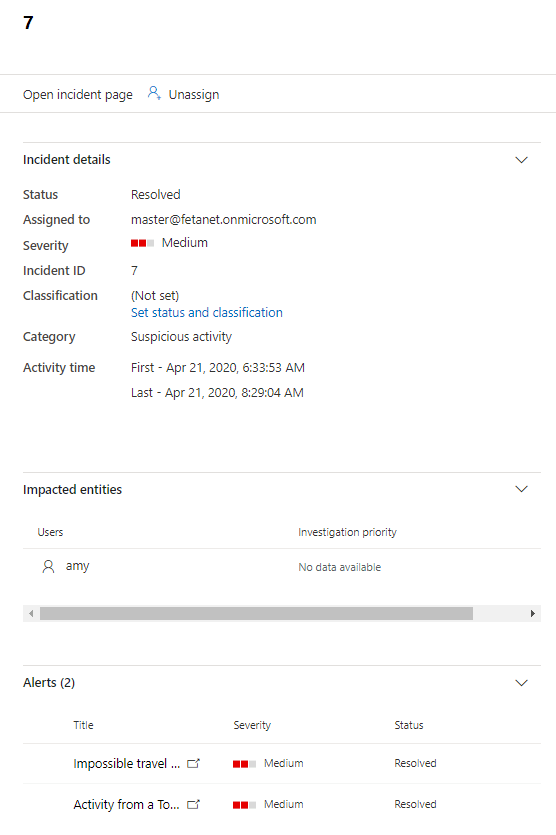
Example 1 – Microsoft Defender ATP Incident
Defender ATP incident is naturally found from “Microsoft Defender Security Center” portal.
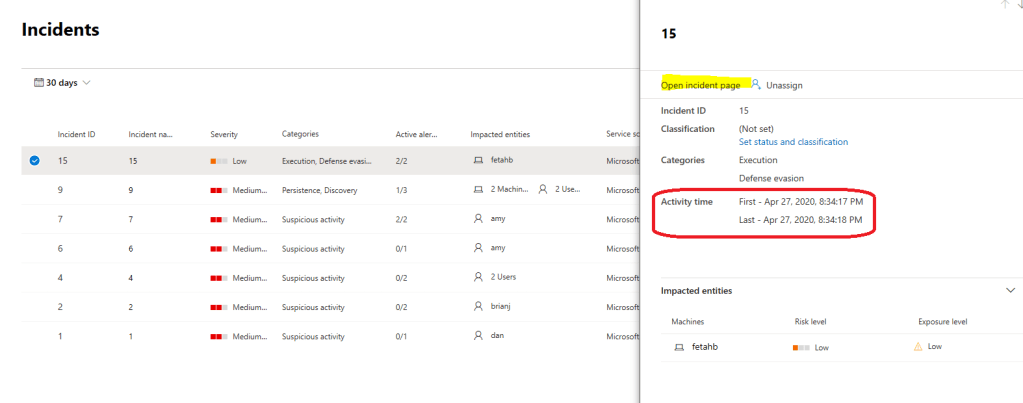
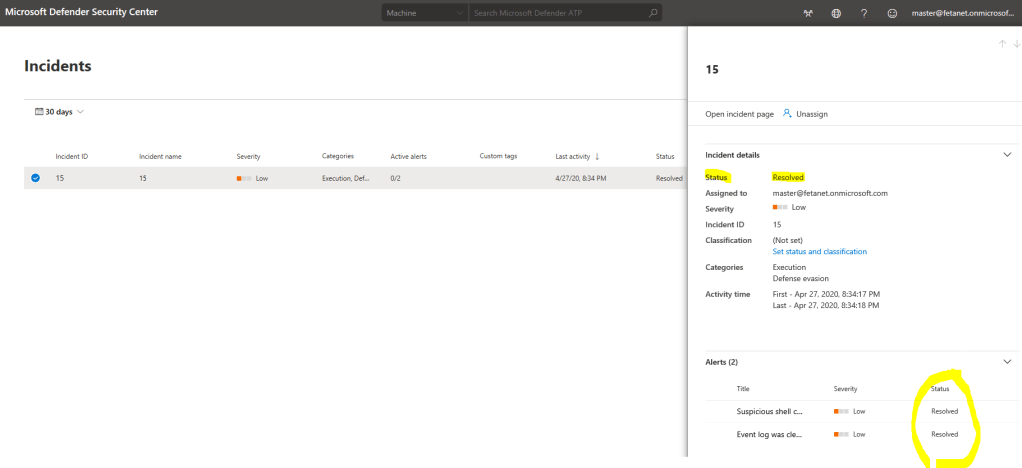
The same incident is also found from M365 Security Center, where it can be also managed underneath “manage incident”.
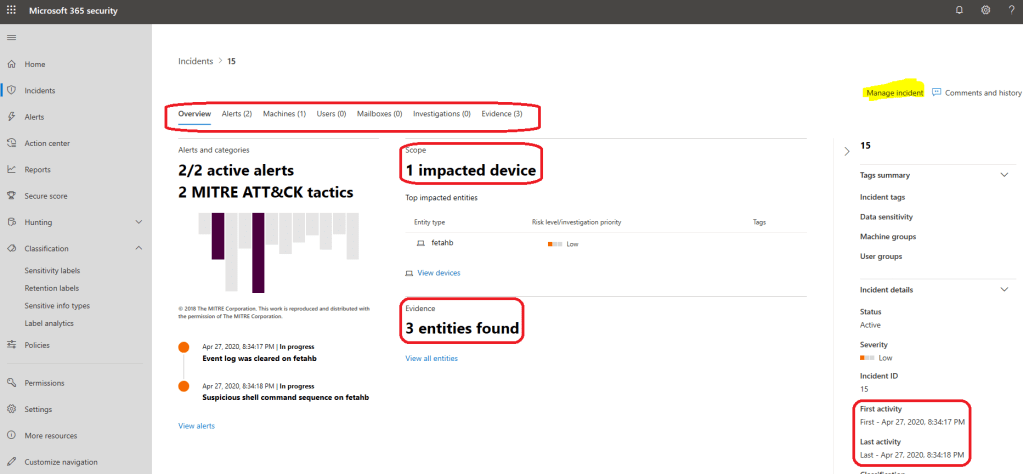
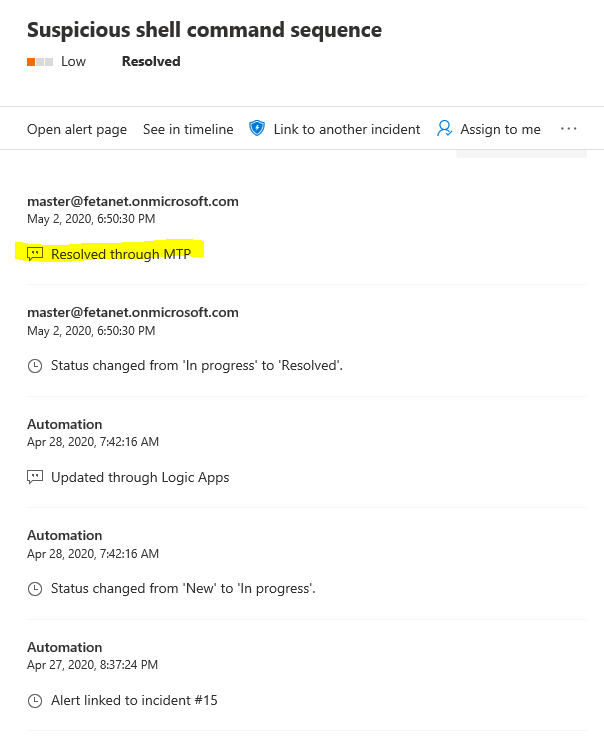
When you click “manage incident” you land to the Incident page where you can find all the necessary information related to the incident. As you can see, the activity times are identical in both Security Centers.
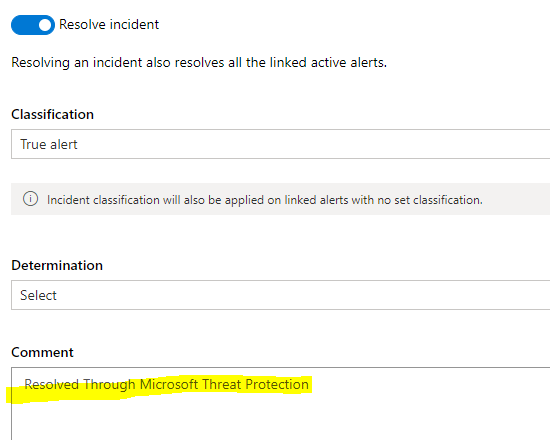
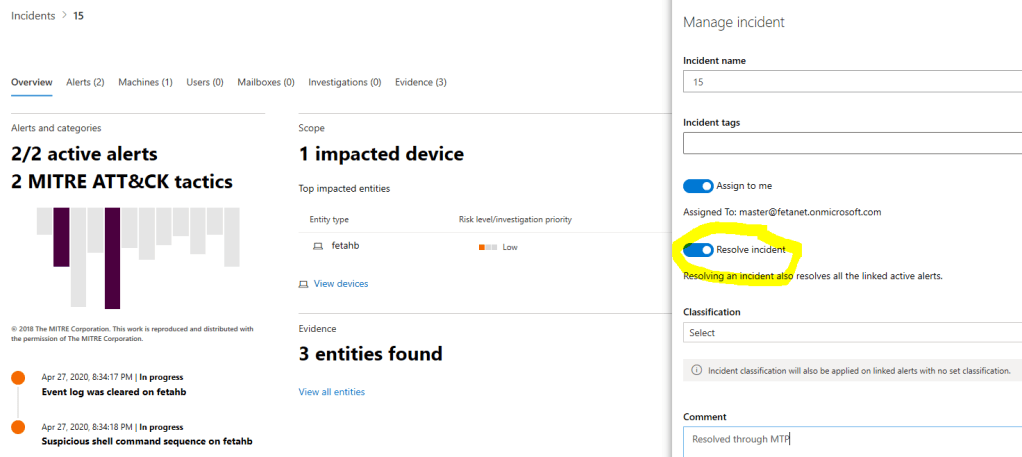
When you resolve the incident from M365 Security Center through MTP capabilities it’s resolved from both
- M365 Security Center aka Microsoft Threat Protection
- Microsoft Defender Security Center
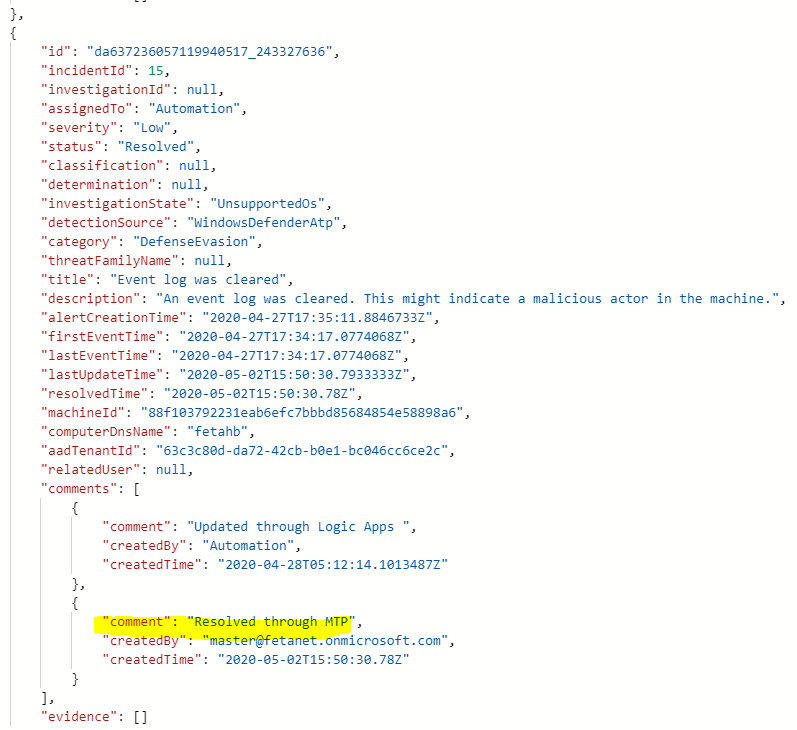
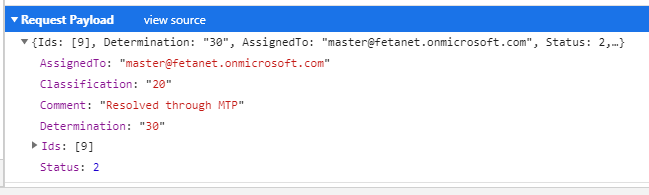
What’s happening behind the scenes…
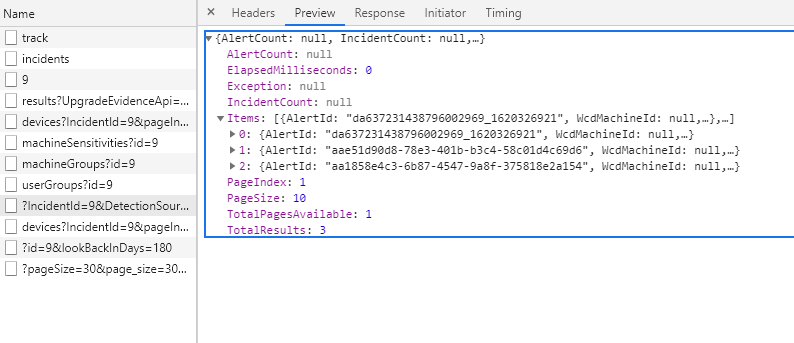
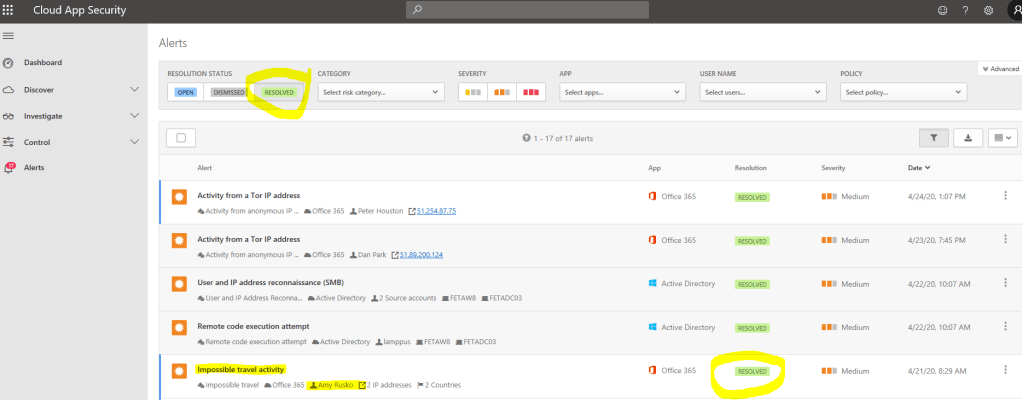
Example 2 – Microsoft Cloud App Security Incident
In the second example, we have the MCAS incident in MTP which contains Cloud App Security alerts (MCAS doesn’t have incidents) in Microsoft Threat Protection (security.microsoft.com) portal.
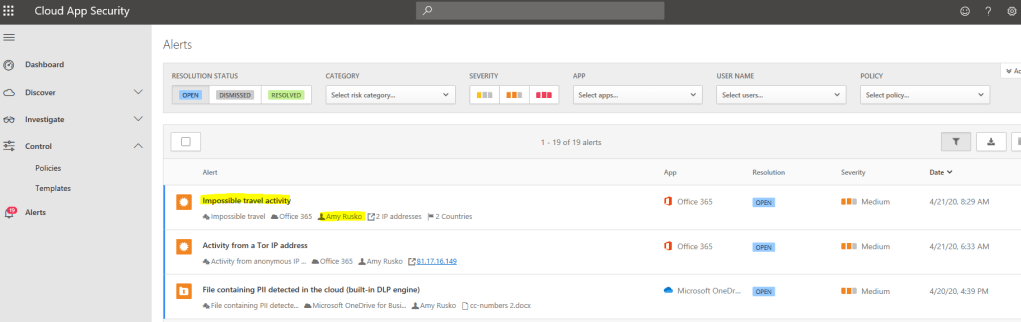
The same alert is naturally found from Cloud App Security portal.
After resolving incident (which also resolves open alerts) we can see that all detections are resolved in both MTP & MCAS, just splendid:)
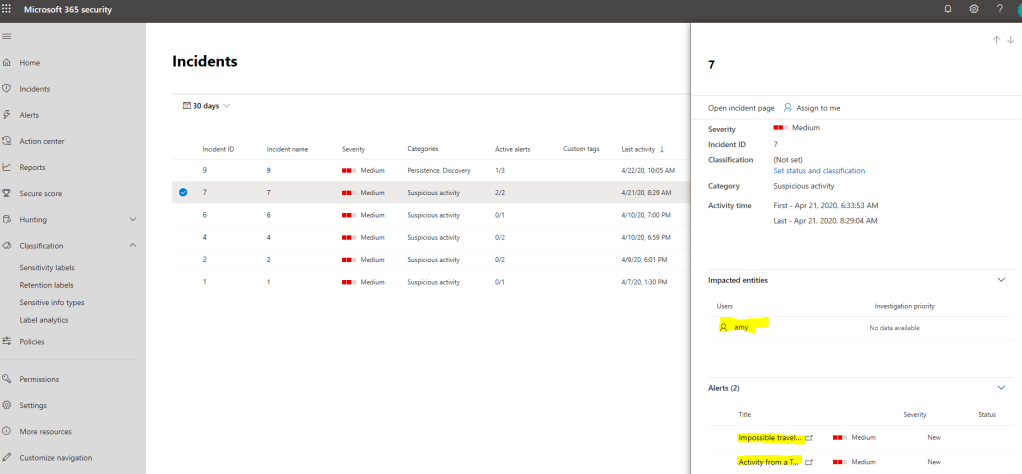
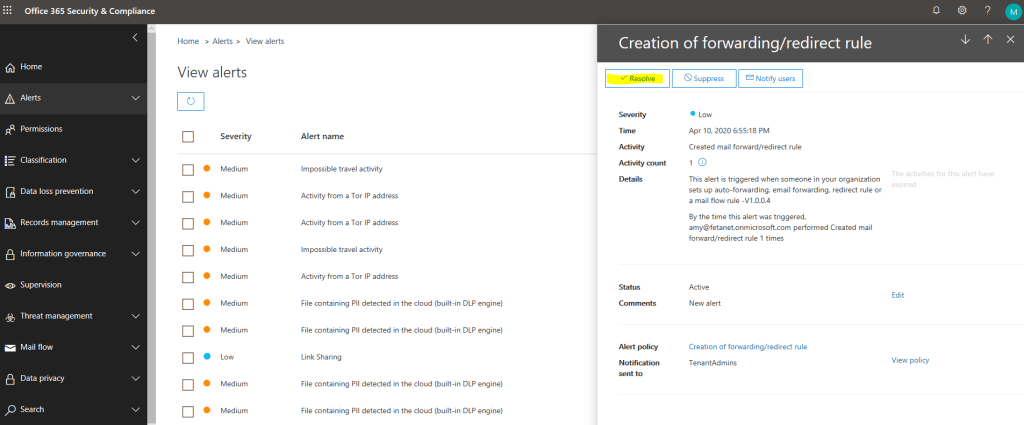
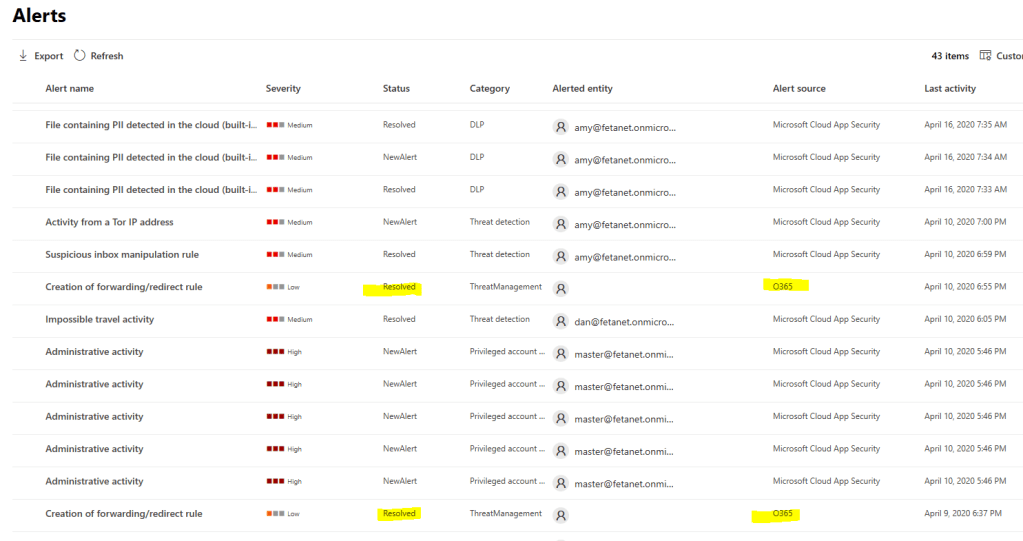
Example 3 – O365 Security & Compliance Center Alert
If you manage the alerts in the MTP portal you can see that the alert contains link to the detection source, to M365 Security & Compliance Center in this case.
Here is a slight difference to earlier examples (to incident management), the alerts cannot be modified in the MTP portal. On the alert page, there is a link to the O365 Security & Compliance portal where alert needs to be managed.
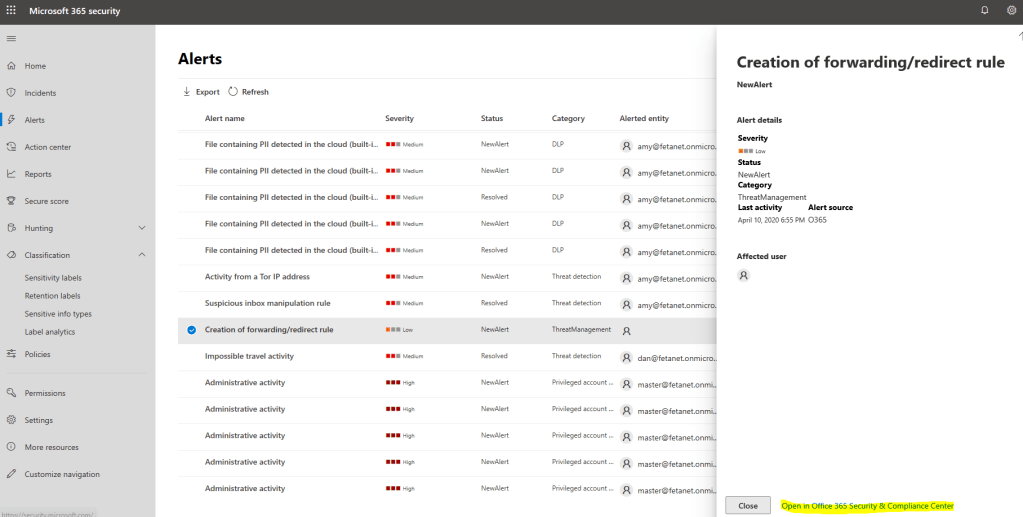
When you resolve the alert from O365 Security & Compliance Center, the alert status will be synced to MTP. Again, this a brilliant feature which I have been missing a lot.
Intelligent Security Graph
According to Microsoft: to be successful with threat intelligence, you must have a large diverse set of data and you have to apply it to your processes and tools.
The data sources include specialized security sources, insights from dark markets (criminal forums), and learning from incident response engagements. Key takeaways from the slide:
- Products send data to graph
- Products use Interflow APIs to access results
- Products generate data which feeds back into the graph
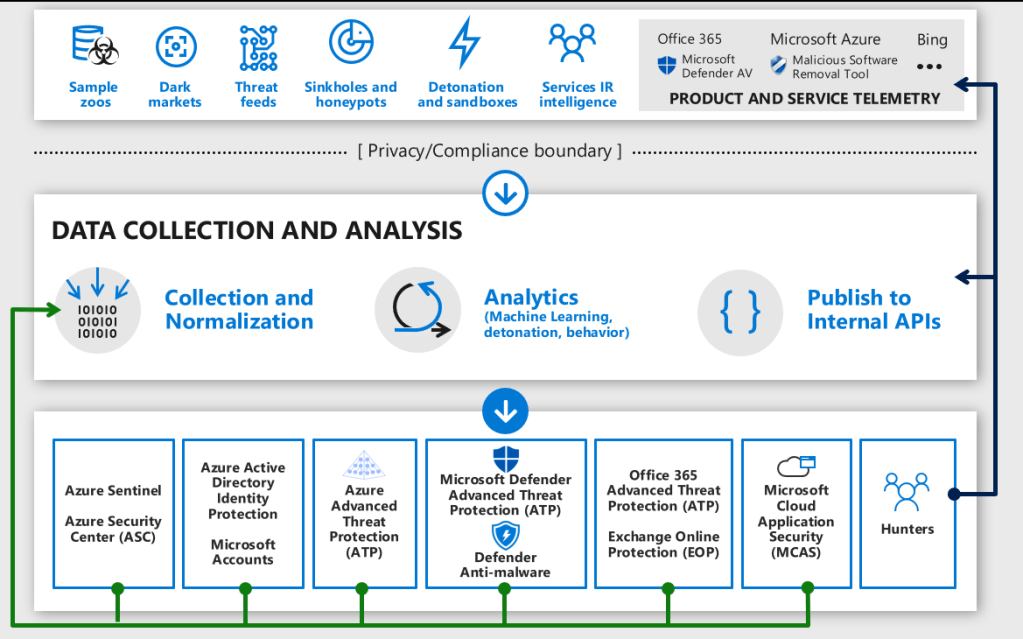
In later blog posts, I will dig more deeply into the Security Graph features. At the time of writing, the following solutions are providers to the ISG (GET & PATCH):
- Azure Security Center (ASC)
- Azure AD Identity Protection (IPC)
- Microsoft Cloud App Security (MCAS)
- Microsoft Defender ATP (MDATP)
- Azure ATP (AATP)
- Office 365
- Azure Information Protection
- Azure Sentinel
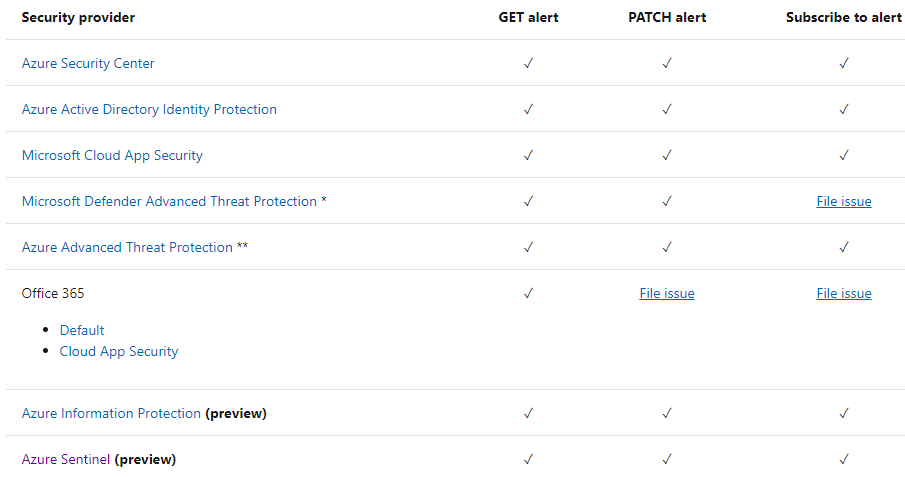
With the alert update capability, you can sync the status of specific alerts across different security products and services that are integrated with the Microsoft Graph Security API by updating your alerts entity.
Support for GET alerts, PATCH alerts (updates are available via the Microsoft Graph Security API but might not be exposed in the provider’s management experience).
Note: Unfortunately, it seems that alert status is not synced back from ISG to the security solution itself which means that even you updated the alert status in ISG it will remain open in the ISG providers (Identity Protection, Cloud App Security etc.). I tested with the following security solutions:
- Azure Sentinel
- Azure Security Center
- Microsoft Cloud App Security
- Microsoft Defender ATP
- Azure AD Identity Protection
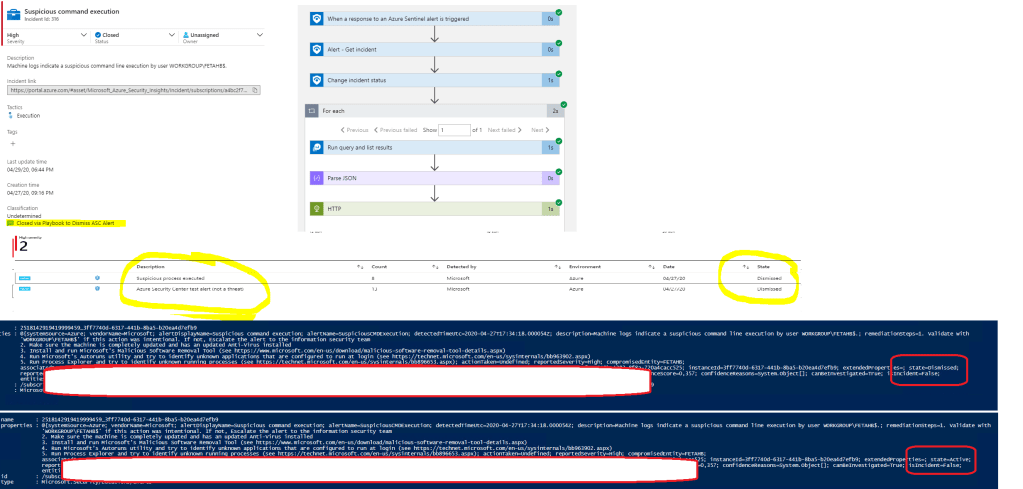
Azure Sentinel Playbooks
With Azure Sentinel Playbooks and SOAR capabilities, there is a possibility to manage incidents and alerts through security solution API’s. In such scenario, you most propably need quite many Playbooks and lots of planning to build integrations which fit to your scenario.
Below is one example, where:
- Alert provider is Azure Security Center
- Azure Sentinel Playbook (Logic Apps) is used to close incident from Sentinel and Azure Security Center
- Playbook template “Close-Incident-ASCAlert” is used created by @SwiftSolves
Conclusion
I was stunned in a positive way to realize M365 and MTP suite capabilities in incident & alert management. There are still some gaps but most probably M365 MTP suite development pace is staggering as with many other products.
I have seen scenarios where alerts are integrated and managed directly with the security solution API. Totally doable but not covered in this blog post. I will address API’s in later posts.
Until next time!


Very good article, Sami Lamppu.
Very complete and detailed.
But I was left with a question that maybe you can contribute.
I have the solutions in my environment and I’m in doubt about how to centralize everything.
I have Azure Sentinel receiving the Defender Atp, MCASB, Azure ATp, Office 365 ATp logs, among others.
I also have MCAS integrated with Azure ATP.
The question is. Where should all technologies be centralized?
That is, if I use Microsoft 365 Security Center to centralize Defender ATP, Azure ATP, MCAS and Office ATP, does it still make sense to receive these logs in Sentinel?
Would it be possible to integrate alerts generated in Sentinel with Microsoft 365 Security Center?
If I receive the solution logs on Sentinel, what would be the meaning of Microsoft 365 Security Center? Can I work with both, centralizing the solutions in both?
I know that there may not be a final answer, but I would be happy to get your position.
Thank you.
Hi Luiz,
It would be a long reply so would it be okay if I send it to your email?
Regards,
Sami
i am interested in the (long) answer as well.
same situation as described by Luiz.
thanks in advance
Can you share a copy as am also having similar queries
Hi Munesh,
Send me an email with your queries and I will get back to you (samilamppu@hotmail.com).
Thanks,
Sam
Hi Sam,
Am helping my organization to effectively use the M365 subscription. Am helping them build a security dashboard. Most of the alerts are distributed in various portals. Have you been successful in creating one single dashboard of alerts OR which is a best portal to look at for maximum alerts.
Regards
Munesh
From: Sam’s Corner
Reply-To: Sam’s Corner
Date: Thursday, October 29, 2020 at 9:50 PM
To: Munesh Ahuja
Subject: [New comment] How To Manage Security Alerts In Microsoft 365
Sami Lamppu commented: “Hi Munesh, Send me an email with your queries and I will get back to you (samilamppu@hotmail.com). Thanks, Sam”
Thank you for your email. I will get back to on next week!
I have all the proper licenses for the security endpoints. I would like to centralize all the alerts on the Microsoft 365 security center. I have been receiving alerts on all the endpoints individually but the incidents in the security center only show the alerts from the Microsoft defender ATP . Are there any integrations involved?
There are actually a lot of integrations needed behind the scenes but mostly between the products, not with the M365 Defender. Some of them are ready to use out of the box and some you need to manually enable, or at least check that those are enabled.
To clarify, you want to have all incidents in M365 Defender (for Microsoft Threat Protection)? M365 Defender is enabled nowadays automatically if you have proper licenses in place.
I want to have all the alerts/incidents on the Microsoft 365 security center from all the different products like Microsoft defender ATP, Cloud app security, Office 365 protection and compliance,etc. Let me how can this be done.
Alerts should be there without any additional integrations when licenses are in place. Have you confirmed that you don’t have any additional filters on?
No we don’t have any filters turned on. One more thing on the Microsoft 365 security center I can just see the incidents tab and no alerts tab is there?
Is it a licensing issue?
That’s his it should look like, alerts tab was removed a couple of months ago. Confirm from the settings tab (general) that there isn’t ’enable’ toggle turned off.
Anyway, This toggle should be already removed from the portal and M355 Defender should be enabled when the correct license level is activated in the tenant.
Hello Sami,
Unfortunately, to resolve the alerte we still having to go into both locations “MCAS” and “Security & Compliance Microsoft 365 portal” to resolve tickets. According to this document (https://docs.microsoft.com/en-us/Office365/SecurityCompliance/alert-policies#viewing-cloud-app-security-alerts) it says “Changing the status of a Cloud App Security alert in the Security & Compliance Center won’t update the resolution status for the same alert in the Cloud App Security portal. For example, if you mark the status of the alert as Resolved in the Security & Compliance Center, the status of the alert in the Cloud App Security portal is unchanged. To resolve or dismiss a Cloud App Security alert, manage the alert in the Cloud App Security portal.”
It doesn’t seem like the sync works either way. No matter which area you resolve an alert in, you still have to navigate to the other manually and resolve the same alert again. Is there any plan to integrate these two areas so our efforts to track alerts and resolve them are not duplicated? Or anyway to have them only generated in one area?
Thank’s a lot for your help
Hello!
Thank you for the feedback and points you raised up. It has to be taken into account that the blog has been written several months ago and in M365 Defender (former MTP) has been several changes since then.
Also, I’m planning to write an updated version of the blog that contains new solutions names and features. And finally, to your highlighted topics, I will test those and get back to you