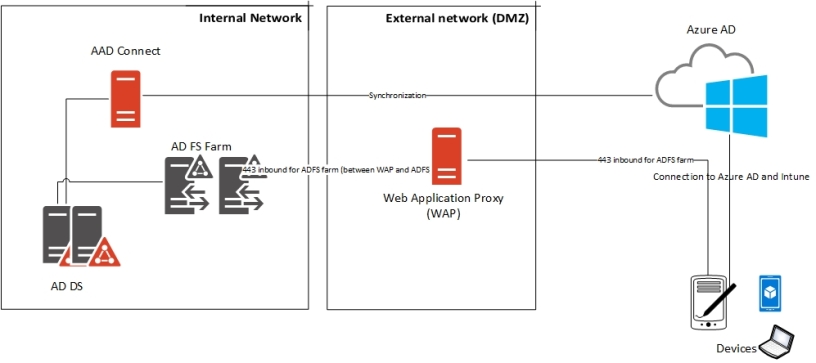
There has been growing trend to get rid of ADFS among many organizations. Reasons vary, there are still scenarios where ADFS is extremely good such as single sing-on with 3th party applications.
When considering to replace O365 relaying party trust and ADFS alternative solutions are:
- Pass-through authentication (PTA) with Seamless SSO
- Password Hash Sync (PHS) with Seamless SSO
- Both above without Seamless SSO
Take into account that there are scenarios where PTA or PHS with SSO might have issues:
- PTA doesn’t support detection of leaked credentials
- Azure AD Domain Services needs PHS to work, so if using only PTA AAD DS is not supported
- PTA is not integrated with AAD Connect Health
The Environment
This specific environment doesn’t have strict security policy requirements and authentication can performed on the cloud (PHS with SSO selected). From user experience PHS & SSO and PTA with SSO are very near each others even the authentication process varies.
In this particular case migration is performed once for all users. At Ignite conference Microsoft announced staged authentication migration option which would provide alternative approach for migration. I just couldn’t find any documentation about it, here is link to session Youtube video.
If you search guidance migrating ADFS to PTA & SSO here you go. My environment contains ADFS farm installation with two ADFS servers, two WAP servers and AAD Connect version 1.882.00.

Pre-Requirements
Azure AD Connect ADDS connector account needs following permissions to on-premises AD to be able to synchronize password hashes.
- Replicate Directory Changes
- Replicate Directory Changes All
How to set these permissions – check my earlier blog post, or run these assuming that you have regularly updated your AAD Connect.
- Set-ADSyncPasswordHashSyncPermissions -ADConnectorAccountName “<aadc service account” -ADConnectorAccountDomain <domainname>
Validate current user sign-in settings from Azure AD
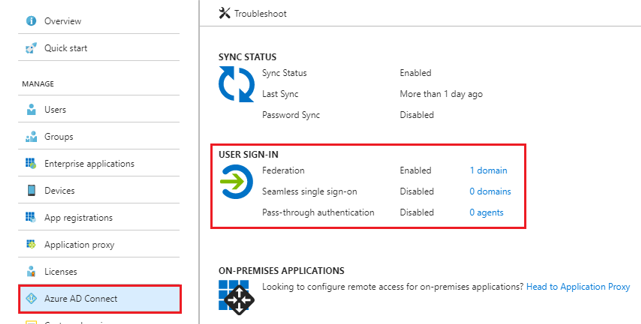
Verify AAD Connect settings, in my environment PHS is already enabled and necessary permissions configured earlier.
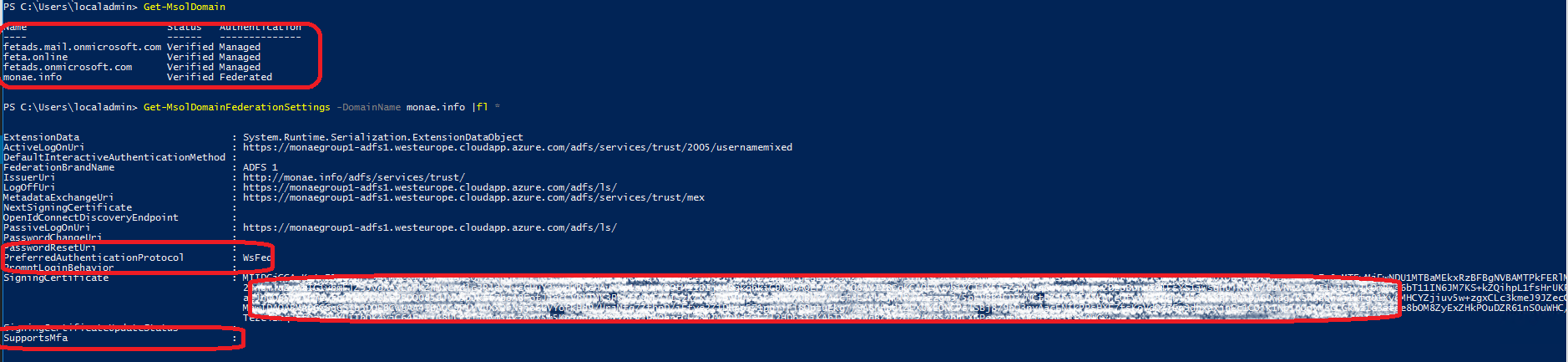
Validate any setting that might have been customized to your Federation design and deployment documentation, specifically the highlighted (PreferredAuthenticationProtocol, SupportsMFA, PromptLoginBehavior), in the event that you need to roll back:
Considerations
- Depending of the number of users, Password Hash Sync operation can take from minutes to several hours. Referring to Microsoft guidance in 20k users environment operation takes approximately 1 hour.
- Validate ADFS usage carefully before implementation
- Is ADFS used for other applications?
- Is it customized?
- Are you using legacy authentication block via ADFS?
- 3th party MFA providers integrated to ADFS?
- Access Control Policies in use?
- InsideCorporateNetwork claim used?
For all of these scenarios there is a workaround available which I do not cover ins this post, more information from Microsoft migration whitepaper.
Plan Migration Method (from Microsoft whitepaper)
Depending how ADFS has been originally configured there are two methods available for migration.
- Using Azure AD Connect. If AD FS was originally configured using Azure AD Connect, then the change to Password Hash Sync as the user sign-in method must be performed through the AzureAD Connect wizard. When using Azure AD Connect, it runs the Set-MsolDomainAuthentication cmdlet for you automatically when you change the user sign-in method, and hence you have no control over it un-federating all of the verified federated domains in your Azure AD tenant.
Note: At this time, you cannot avoid un-federating all domains in your tenant when you change the user sign-in to Password Hash Synchronization when AAD Connect was originally used to configure AD FS for you. - Using Azure AD Connect with PowerShell. This method may be used only when AD FS was not originally configured with Azure AD Connect. You still need to change the user sign-in method via the Azure AD Connect wizard, but the core difference is that it will not automatically run the Set-MsolDomainAuthentication cmdlet for you as it has no awareness of your AD FS farm, and hence you have full control over which domains are converted and which order.
Before going forward this is the point where you need to confirm that ADFS documentation is up to date and backups are taken (and working).
ADFS backup can be taken with ADFS Rapid Restore tool. At minimum export “Microsoft Office 365 Identity Platform” relaying party trust settings.
Implementation
- Enable Password Hash Sync
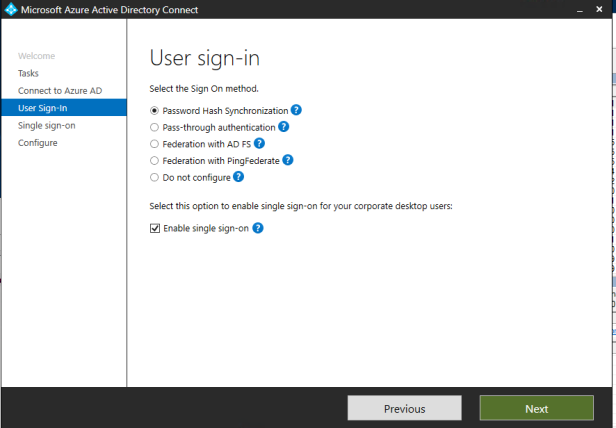
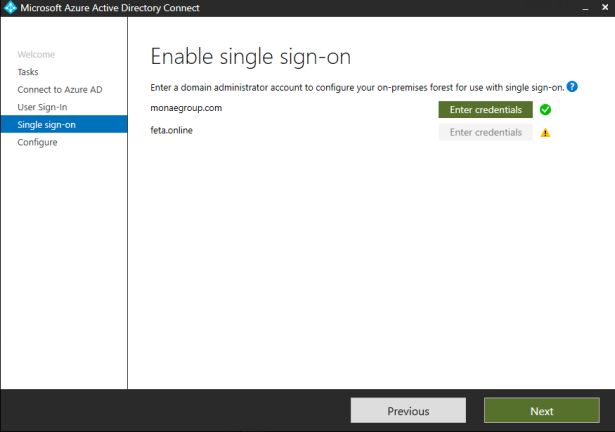
- Enable Seamless Sign On
- Change sign-in method to PHS and Seamless SSO
Enable PHS
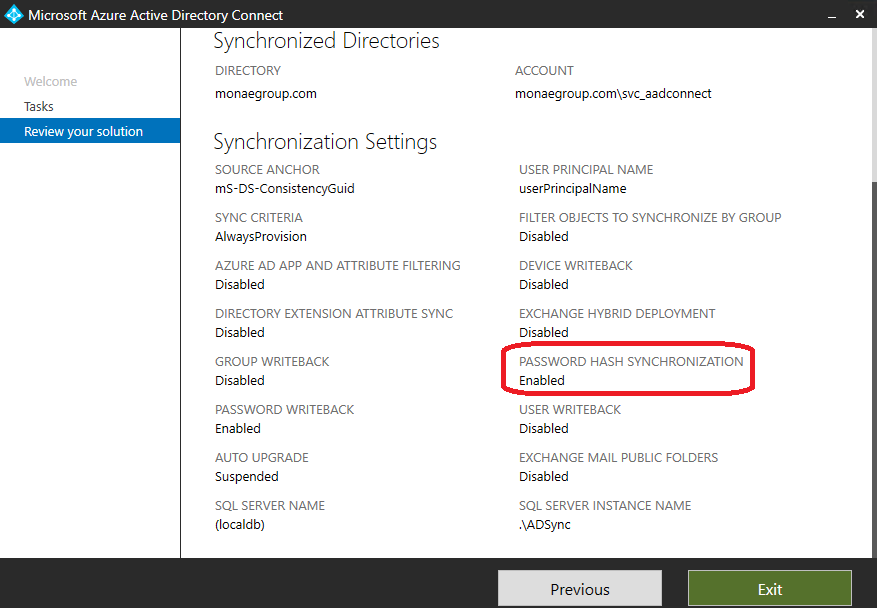
As seen below, it’s already configured. If deployment is needed in your environment run AAD Connect wizard and enable PHS. Remember to grant permissions to AADC ADDS Connector account before configuring AAD Connect.

Validate PHS has completed successfully
Couple options here:
- Use Event Viewer and application logs
- Use Azure AD Connect wizard troubleshooting task
Prepare for Seamless SSO
To your devices to use Seamless SSO, you need to add an Azure AD URL to the users’ Intranet zone settings by using Group Policy in Active Directory. Add these URL’s to Local Intranet zone (value in GPO = 1)
- https://autologon.microsoftazuread-sso.com
- https://aadg.windows.net.nsatc.net
- For Mozilla “about:config” → network.negotiate-auth.trusted-uris → add “https://autologon.microsoftazuread-sso.com”
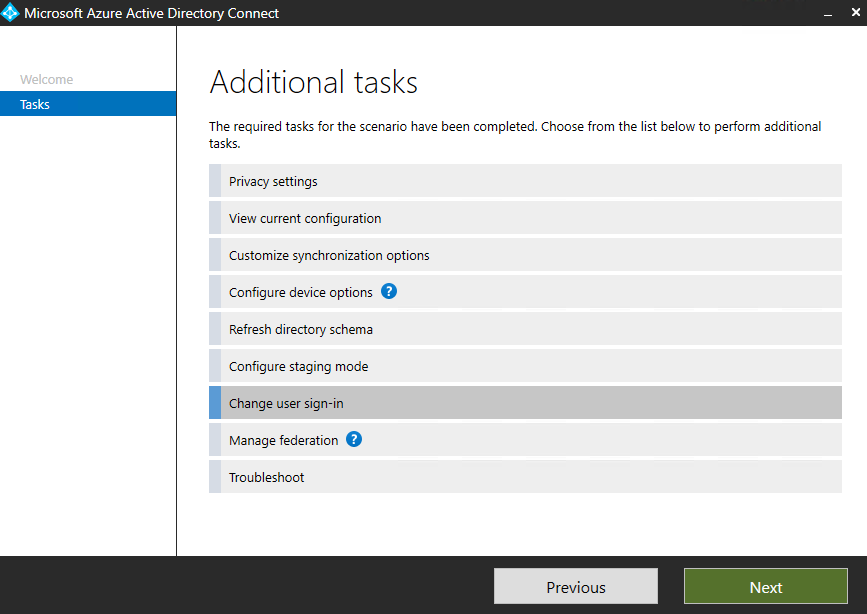
Change Sign-in method to PHS and Enable Seamless SSO


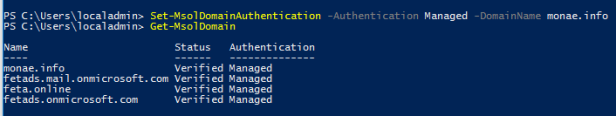
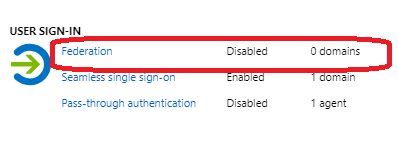
Test Authentication with PHS
Now, after configuration change I’m landing to Azure AD login page instead of ADFS because my tenant is configured to use Password Hash sync.
To test PHS functionality and avoid Seamless SSO I opened browser In-Private mode and navigated to O365 login page (portal.office.com) with my test user and are able to login with my UPN and password to the portal. Everything works as expected.
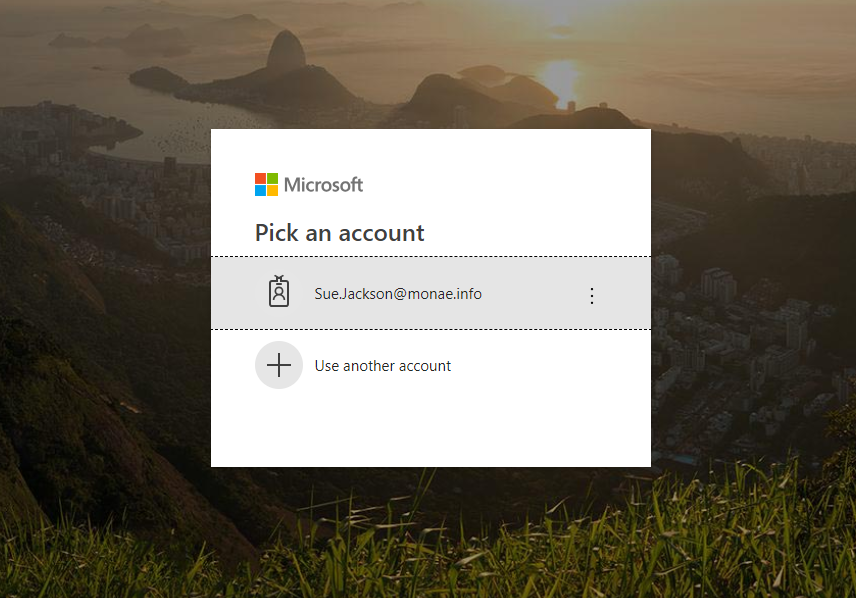
Test Authentication with Seamless SSO
From Internal network open IE and navigate to portal.office.com where credentials are asked. Save persistent token to get smooth authentication experience at future.
Take in to account that portal.office.com doesn’t support currently domain hint and therefore UPN is needed.
If using services that supports domain hint SSO works as expected, examples:
- Access panel – https://myapps.microsoft.com/contoso.com
- Outlook on Web – https://outlook.office365.com/contoso.com
- Office 365 portals – https://portal.office.com?domain_hint=contoso.com, https://www.office.com?domain_hint=contoso.com
And also if an application sends sign-in requests to Azure AD’s tenanted endpoints instead of common endpoints, link to reference.
- SharePoint Online – https://contoso.sharepoint.com
- Azure portal – https://portal.azure.com/contoso.com
Summary
Password Hash Sync with Seamless SSO provides smooth user experience and is good alternative approach when choosing cloud authentication model. As said, ADFS has still its place if it’s used heavily for SSO to 3th party applications.
hello thanks for the great article. One question: with adsf sso we use sam account name from extern computers (example Smith) and not upn (smith@contoso.com) – does this work with seamless sso?
thank you and greatings
Jim
PS: I am not shure if I should use PTS or PHS, we have ca. 1000 users
Hello Jim,
I would go with PHS. Not related to the number of user rather the simplicity it brings along. Most of clients i’m working with have decided to move forward with the PHS. Seamless sso is opportunistic approach and how it works in detail can be found from here
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso-how-it-works